The "Free" Lie: 12 AI Tools That Are Actually Free (No Trials, No Credit Cards, No Nonsense)
Tired of getting duped by "free" AI tools that aren't? Here's a verified list of...

The Secret Life of Subdomains 🌐: From Takeover to $$$ Bounties
When most people think of a website, they imagine the main domain: example.com. But hackers know...
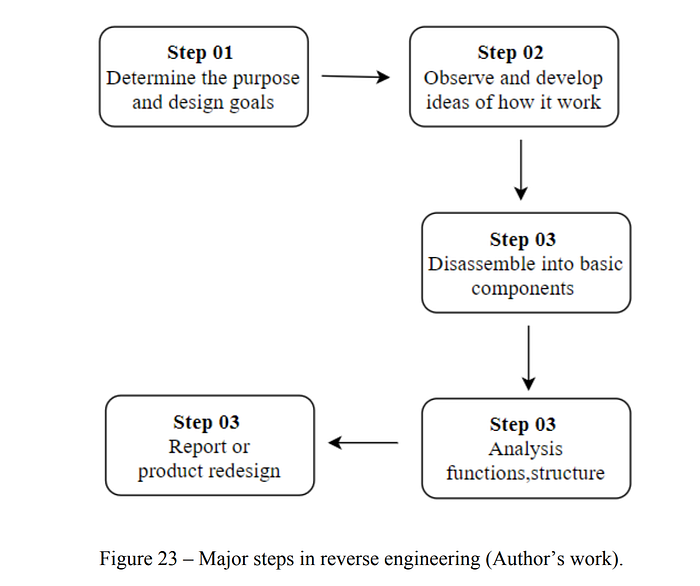
Primary Methods to Reverse Engineering PE Files (.exe Files)
Revere engineering, also called back engineering is the process by which a man-made object is...

💥 From LFI to RCE via PHP Sessions (PHP 5) — A Complete Guide with Real Examples 🧠💻
By Zoningxtr

JS For Hacker , Chapter One-Intro
Java Script For Hacker , Learn To Think Like Hacker

Announcing IWCON 2023 Speakers Fourth Batch
Register today to be a part of the coolest Cybersecurity conference and end 2023 on a bang!

20 Cache Poisoning Case Study | Depth Analysis of Real-world Bug Reports
An in-depth analysis of real-world cache poisoning vulnerabilities discovered on major platforms,...

Mastering Blind XSS: Real-World Techniques for High $Bounties
From simple dorks to advanced metadata injection, here's a complete walkthrough of the...
Post-Exploitation Toolkit: 25 Commands Every Hacker Uses (Step-by-Step Guide)
✨ Link for the full article in the first comment

Client Side Path Traversal (CSPT) Bug Bounty Reports and Techniques
Over the past year, CSPT bugs have gained significant attention, with numerous blogs and...
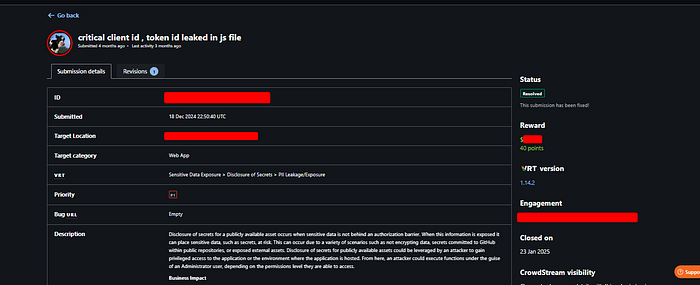
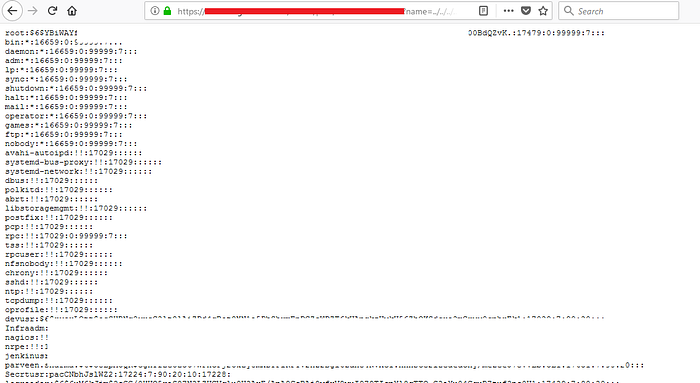
"Unveiling Hidden Treasures: How Analyzing JavaScript Files Led Me to Tokens and Secret Keys"
Before diving in, I'd like to ask everyone to take a moment and pray for our brothers and...

How I Found a $2,800 Bug in 60 minutes — and How You Can Spot It Too
The $2,800 Bug That Took Just 1 Hour to Find
LFI to RCE: Mastering the Step-by-Step Path from File Inclusion to Full Shell Access
✨ Link for the full article in the first comment

Hacking APIs Series(24/36) — Broken Function Level Authorization (BFLA)
👋Hey security enthusiasts! 🚀

The Rebus Code: Unveiling the Secrets of Regex in R
In the intricate world of data analysis, the task of text pattern recognition and extraction is...

Complete Guide to Dnsx for Mass DNS Resolution and Bug Bounty
Essential guide to mass DNS resolution, takeover detection, and sensitive records in bug bounty...

My 5-Minute Workflow to Find Bugs on Any Website
A step-by-step guide to my most effective, shortcut methods for bug bounty hunting.

Top 25 Race Condition Bug Bounty Reports
In this article, we will discuss Race Condition vulnerability, how to find one, and present 25...

JS Link Finder Burp Suite Extension Guide
Improve your bug bounty hunting, pentesting, and appsec skills with the JS Link Finder Burp Suite...

🚀 $3,000 for Finding a Hidden Subdomain: My Reconnaissance Success Story 💸
When I first got into bug bounty hunting, I used to think finding big bugs required fancy...

🚀 From Zero to $100K: How to Become an AI Hacker in 6 Months (While Everyone Else Missed the Boat)
You type a simple message into ChatGPT, and suddenly it spills its entire system prompt, reveals...

How I got my first $13500 bounty through Parameter Polluting (HPP)
This write-up is about 2 IDORs and an XSS I found on a housing website. However what led me into...
Stealthy Recon: Master Passive Information Gathering for Pentesters Step-by-Step
✨ Link for the full article in the first comment

Actuator Unleashed: A Guide to Finding and Exploiting Spring Boot Actuator Endpoints
A hands-on walkthrough to find, test and exploit Actuator endpoints for bug hunters.
How I Turned a Headless Browser into a Critical SSRF Goldmine
Three months. That's how long I stared at bug bounty programs, submitting low-risk findings...
One Random Recon, One Real Bounty
From countless dead ends to a single Swagger UI payload — the unexpected breakthrough that...

The Ultimate Payload Checklist for XSS, SQLi, LFI, and SSTI
A practical, hands-on checklist of advanced XSS, SQLi, Path Traversal, and Code Injection...
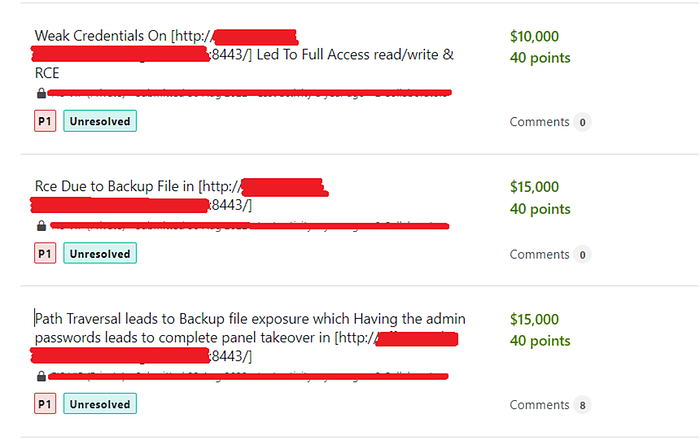
A Journey of Limited Path Traversal To RCE With $40,000 Bounty!
#Introduce Myself:

Hidden API Endpoints: The Hacker's Secret Weapon 🔍
I'm a cybersecurity enthusiast and the writer behind The Hacker's Log — where I break down...

Blind XSS through PasteJacking: A Detailed Guide to Clipboard Exploitation
Discover how attackers abuse clipboard paste handling to trigger Blind XSS from setup to...