Read for Freee..ee.e
🐺Hunters,
I hope you're learning something which can be helpful in your bug hunting journey.
Kindly refrain from scammers who just copy other's article and use some sentences on their own, just like @ibtissamhammadi1 this guy. He copied my full article 503 Page to Critical Bug and use some sentences of his own.
Introduction
This finding is related to previous bug of 503 Page to Critical Bug. I recommed reading this article before/after this one:
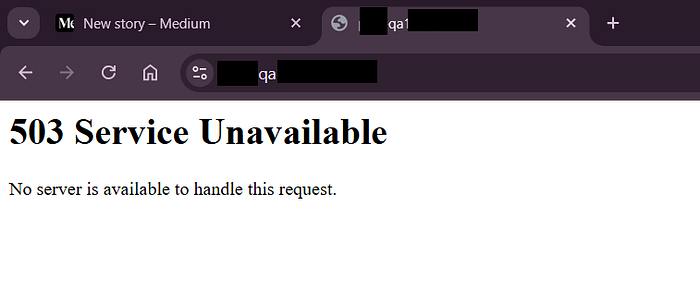
Previously Experienced with 503 Service Unavialable Page, I chose this subdomain again without any thought of something like previous Bug.
Subdomain
I was going through the subdomains list of my target and I noticed there is one subdomain with 503 Service Unavailable Page.
I started with google dorking, waybackurls, and virustotal recon but find nothing. If you are interested in these recon techniques read these articles:
Hunting
I started hunting with my usual directory enumeration with dirsearch:
dirsearch -u https://sub.target.com/ -f -F -x 403 -t 3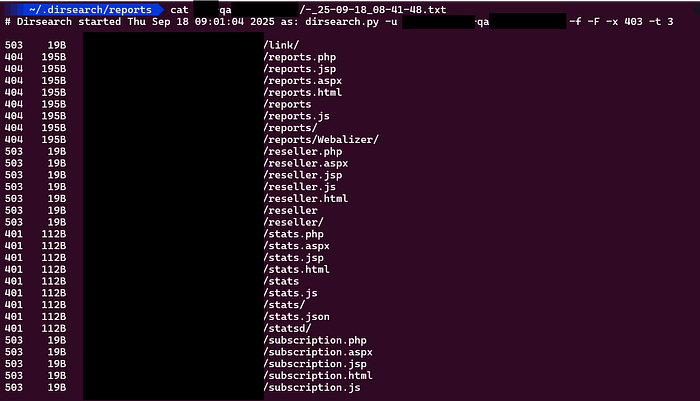
As you can see in the above image, there are many directories and files with 404 response code like /reports and /reports/Webalizer/ directory, I also enumerated on these directories but found nothing good. Other is 401's in which I didn't get the username&password for login.
Large Wordlist
I started enumeration again with seclist's large direcotries list.
dirsearch -u https://sub.target.com -w /usr/share/seclist/Discover/Web-Content/raft-large-directories.txt -F -x 403 -t 3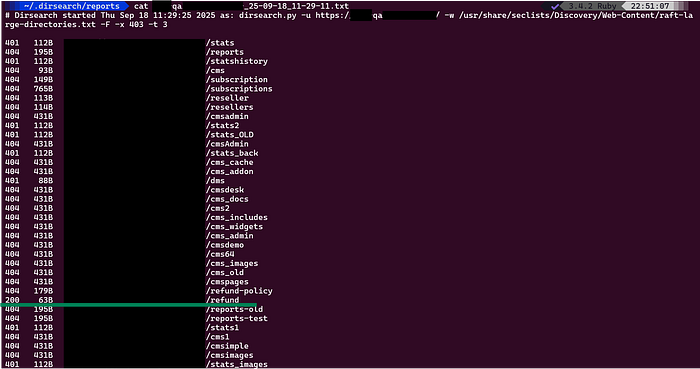
As you can see in the image, there is one directory named as /refund hits 200 OK response code.
I quickly opened this /refund endpoint in my browser to see the page.
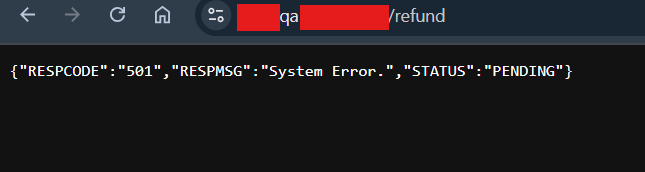
I don't have any idea other than enumeraation on this /refund endpoint.
Refund API
I started again with my dirsearch on this /refund endpoint but with dirsearch's default wordlist using -f signal.
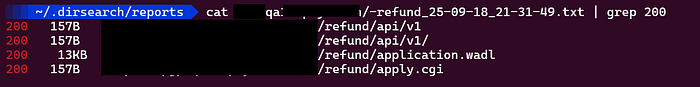
As you can see in the above image, there are three same response with 157B along side 200 reponse code. They are returning same response like above of /refund endpoint.
But when I open application.wadl file in the browser, it's showing minimal API paths and after some time, I found a parameter named as "detail=true" which gives full exposure to Refund API along with it's sub-endpoints and METHODS, check image below:
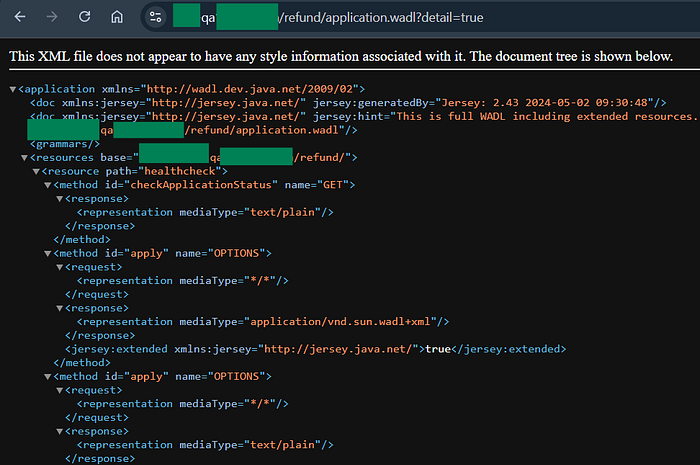
Report
I reported this issue to security team and they said it's fall out of scope because it's an QA environment based subdomain.
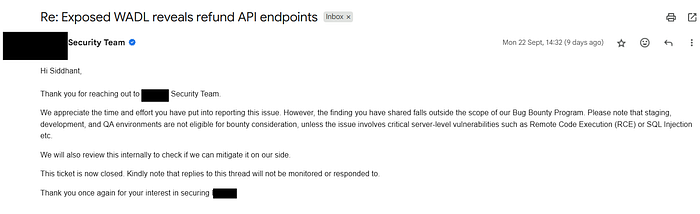
They eventually restricted the API exposure and fixed the issue after some time.
Enjoyed the read?
If you learn something or this article is helpful for you, as a token of appreciation you can send me:
50 claps, a comment and share everywhere.
Let's connect — I share more insights, bugs, and write-ups on


