👋 Hey, I'm Vipul
I'm a cybersecurity enthusiast and the writer behind The Hacker's Log — where I break down how real hackers think, find, and exploit vulnerabilities (ethically, of course 😎).
In today's deep-dive, let's uncover one of the most powerful — yet underrated — hacker secrets: Hidden API Endpoints.
Hackers' Recon Guide (detailed, practical, downloadable) → https://thehackerslog.gumroad.com/l/hackersreconguide
🧩 What Are Hidden API Endpoints?
Every web app relies on APIs — those invisible bridges connecting your clicks to the database. But here's the twist: not all endpoints are visible. Some are hidden or undocumented, like:
/api/v2/internal/users/api/admin/deleteUser/api/dev/test_endpoint
These are internal routes developers use for debugging, testing, or staging environments. They often don't appear on the UI, but they still respond if you know where to knock. 🚪
And that's what makes them gold for bug bounty hunters and pentesters.
🧠 The Hacker Mindset: Think Like a Developer
Hidden endpoints exist because of developer habits.
When building an app, developers:
- Keep staging APIs live even after launch 🧱
- Forget to delete debug or admin routes 🧑💻
- Leave unlinked endpoints for mobile or internal dashboards 📱
So, instead of just scanning websites like a robot, you need to think like a dev.
Ask yourself:
"If I built this feature, what would I name the endpoint?"
That's how you start finding the invisible attack surface.
🕵️ Step 1: Passive Recon — Finding the Clues
Passive recon means collecting data without sending aggressive requests. Here's how I do it 👇
🔍 Look Inside JavaScript Files
Developers often hardcode API URLs or endpoints inside .js files.
Use LinkFinder — a tool that extracts endpoints from JavaScript.
# Clone and run LinkFinder
git clone https://github.com/GerbenJavado/LinkFinder.git
cd LinkFinder
python3 linkfinder.py -i https://target.com/static/main.js -o cliIt'll output URLs like:
/api/v1/users
/api/internal/logs
/api/admin/backupCongrats 🎉 — you've just found hidden paths without touching the server.
🕸️ Crawl Archived Pages
The Wayback Machine stores old URLs that developers forgot about.
Use this tool combo:
echo "target.com" | waybackurls | grep "/api/"That one line can reveal long-lost routes like:
https://target.com/api/v1/test
https://target.com/api/dev/loginSometimes, these are still alive. 🧟
⚙️ Step 2: Active Discovery — Knocking on the Door
Once you've collected endpoint candidates, it's time to test them safely.
You can use curl or automated tools like ffuf.
🧑💻 Example 1: Quick Python Probe
import requests
BASE = "https://target.com"
endpoints = [
"/api/internal/users",
"/api/admin/config",
"/api/dev/test"
]
for ep in endpoints:
url = BASE + ep
r = requests.get(url)
print(f"{r.status_code} - {url}")If you get:
200 - https://target.com/api/admin/configYou've just found a live hidden endpoint 😈
⚡ Example 2: Directory Fuzzing
For brute-forcing hidden APIs, I love ffuf.
ffuf -u https://target.com/api/FUZZ -w /usr/share/seclists/Discovery/Web-Content/api.txt -mc 200,301,302It'll try hundreds of possible routes and tell you which ones exist. Just remember: don't go wild — always stay in-scope and respect rate limits. ❤️🔥
🧰 My Go-To Tools 🧠
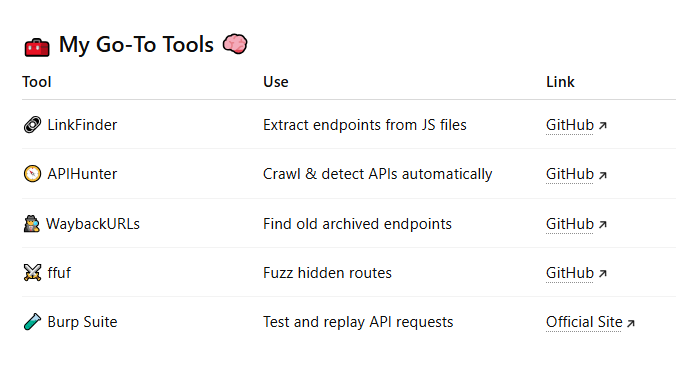
💣 Real-World Example: How I Found a Hidden Admin API
During one of my bug bounty hunts, I noticed a JavaScript file referencing:
/api/internal/exportDataCurious, I sent a GET request — it responded with:
401 UnauthorizedClassic. But then I added an Authorization header copied from a normal user request, and boom 💥 — I got a JSON response with admin-only data exports.
That single hidden endpoint turned into a high-severity bug worth $$$.
Lesson: Never ignore what JS whispers to you.
🧑⚖️ Stay Ethical (Seriously!)
Always:
- Stay within scope of your bug bounty or engagement.
- Never exploit beyond proof-of-concept.
- Avoid hitting live customer data.
- And report responsibly.
Security research ≠ destruction — it's protection through discovery. 🛡️
🧩 Advanced Trick: GraphQL Introspection
Some modern apps use GraphQL APIs — and if introspection is enabled, it's like reading their entire API manual.
Try this:
curl -X POST https://target.com/graphql \
-H "Content-Type: application/json" \
-d '{"query":"{ __schema { types { name fields { name } } } }"}'If you get a response full of queries and mutations — jackpot 🎯 You just discovered the entire schema.
🔍 2. How Hackers Discover Them
Let's walk through the process step-by-step 👇
🔸 a. Using Browser DevTools
Open your target website → Inspect → Network tab → Filter fetch/XHR.
You'll often find requests like:
https://target.com/api/v1/config
https://target.com/api/private/featureflagThese aren't visible anywhere in the UI… but they exist. Boom 💥 — you just found a hidden endpoint.
🔸 b. Using Burp Suite + Wordlists
Use Burp Intruder or ffuf with API-specific wordlists.
Example:
ffuf -u https://target.com/api/FUZZ -w ~/wordlists/api.txt -mc 200,403Try wordlists like: 👉 SecLists API Endpoints 👉 API Fuzz Wordlist (My GitHub)
🔸 c. Leaking Endpoints via JavaScript
Run this one-liner to find API URLs hidden in JS files:
grep -oP '(https?:\/\/[^\s"']+\/api\/[^\s"']+)' *.jsTools like LinkFinder or JSParser automate this beautifully. 💻
🧠 3. Why Developers Hide Them (And Why You Should Care)
Developers sometimes leave these routes in production because:
- "They're for internal use only."
- "We'll remove it later." (They never do. 😅)
- "Nobody will find them."
Guess what? Hackers always find them. Hidden APIs can expose:
- Sensitive user data
- Authentication flaws
- Forgotten admin panels
- Cloud configurations ☁️
🚨 4. Real-World Example: How a $2,000 Bug Was Found
A researcher once discovered an endpoint /api/v2/users/exportAll that exported every user email in CSV.
No auth, no rate limit.
He submitted it via a bug bounty program → $2,000 reward. 💰
This is why recon is everything — the more endpoints you find, the higher your chances.
💡 5. Bonus: Automate Hidden API Discovery
Let's make it easy using Python 👇
import requests
base_url = "https://target.com/api/"
endpoints = ["admin", "v1/users", "private/config", "dev/test"]
for ep in endpoints:
url = base_url + ep
r = requests.get(url)
if r.status_code in [200, 403]:
print(f"[+] Found endpoint: {url} ({r.status_code})")You can find the full script here →
🚀 Want to Level Up Your Recon Game?
If you want a full, hands-on recon playbook — step-by-step with tools, scripts, wordlists, worksheets and real examples — grab my detailed recon guide for hackers and bug hunters here: Hackers' Recon Guide (detailed, practical, downloadable) → https://thehackerslog.gumroad.com/l/hackersreconguide
Check it out for walkthroughs, lab exercises, and everything I use to find high-value targets.
📚 Related Reads (From My Blog Series)
📌 Connect With The Hacker's Log
If you enjoyed this guide, join our growing ethical hacking community for advanced tutorials, case studies, and recon challenges!
🌐 Website: https://thehackerslog.com/
📰 Substack: https://thehackerslog.substack.com/
🛒R
Happy Hunting — and always, hack ethically. ⚔️


